Leveraging IoT security to improve ROI
August 20, 2015

In a standing-room only session at IoT Evolution Developers conference, Alan Grau of Icon Labs noted that security now isn't only a requirement for mo...
In a standing-room only session at IoT Evolution Developers conference, Alan Grau of Icon Labs noted that security now isn’t only a requirement for most applications, but it’s becoming a competitive advantage. With the rash of exploited vulnerabilities in the cyber world in recent years, consumers are being driven towards considering security is now factoring into the purchasing decision of both consumers and enterprise customers, in turn driving top organizations and tier 1s to invest in what has historically been one of the most overlooked aspects of system design.
These investments are non-trivial, on the one hand because most organizations do not have a competency in securing IoT systems, which involves issues of scale (how does your security scale from a system running an 8- or 16-bit MCU up to 32- or 64-bit platforms capable of running linux or android); the regulatory and compliance demands of various safety-critical industries (which are becoming more pervasive as everyday ‘dumb’ devices get connected); a diverse communications landscape that spans from Bluetooth and ZigBee links to Wi-Fi and Ethernet to create widening attack surfaces; and the basic challenges of dealing with fragmented ecosystems comprised of varying hardware and software companies and end users. On the other hand, if adding security as a value proposition that can generate ROI simply requires solutions that are as close to bulletproof as possible.
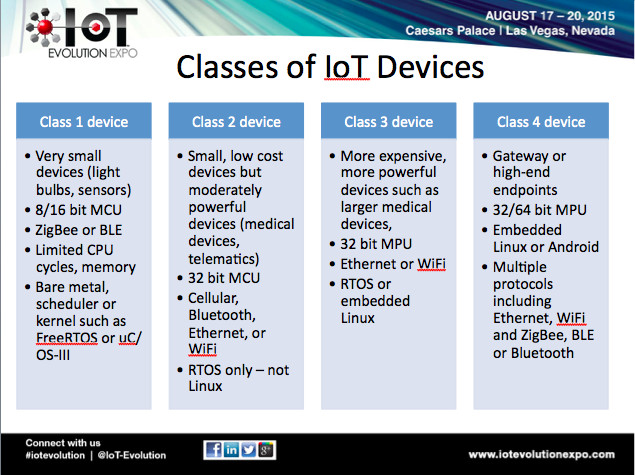
While nearly all of the IoT standards that exist today attempt to address common security issues such as identity management, auditing and protection, attack detection and mitigation, and management and visibility, there is of course no one-size-fits-all answer for security considering that the IoT is comprised of no fewer than four device classes (Figure 1). Comprehensive security for all of these devices must address the following, but each in its own specific way:
- Device hardening through a hypervisor, secure boot, and included intrusion detection, as well as the leveraging of hardware security features
- Data protection that covers both data at rest and data in motion with key and password obfuscation
- Secure communications enabled by secure protocols (such as IPsec), firewalls, and mutual authentication
- Visibility and management through IT system integration that provides the ability to execute policy updates, event detection, etc.
To address these for different device classes, Icon Labs has developed a portable, small footprint security framework for the Internet of Things that is designed for embedded use and carries minimal performance overhead (Figure 2). Some of the most significant features of the framework are on the visibility and management side that provide intrusion detection and prevention (IDS/IPS) capabilities, as well as policy orchestration. The latter is a key to better device management and control features that can be integrated to systems so that designers can put security to use for them to improve ROI. To learn more visit www.iconlabs.com or keep your eyes peeled for Alan’s presentation slides on the IoT Evolution website, available next week.





