Future industrial requirements being met by redefined mid-range FPGAs
April 19, 2017
A sea change is underway in the industrial equipment and manufacturing sector. The renewed call for more jobs and several new mandates for minimum wag...
A sea change is underway in the industrial equipment and manufacturing sector. The renewed call for more jobs and several new mandates for minimum wage hikes are forcing vendors who build automation equipment to respond to a new reality and difficult technology hurdles. They must turn to suppliers that can help them create more efficient, smarter automation solutions that meet a variety of challenging requirements. Among the key new answers to these challenges is a re-defined category of mid-range FPGAs that are purpose-built and specifically architected to reduce the cost, power, and size of industrial automation systems while still delivering a variety of necessary performance, flexibility, and security features.
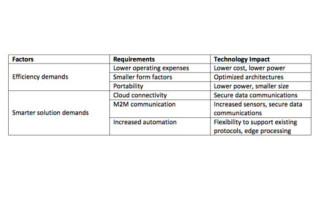
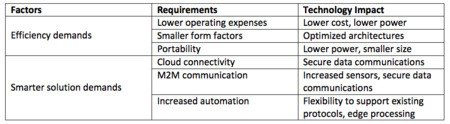
The requirements today’s automation equipment vendors face are shown in Table 1. The challenge presented by these requirements can be divided into two categories: efficiency demands and smarter solution demands. Let’s look at each in detail and provide application examples of how new technology – new mid-range FPGA architectures, specifically – are addressing these requirements.
[Table 1 | Factors and requirements for equipment vendors.]
First, consider the increasing use of robotics to increase human efficiency at a particular task. These human-assisting robots must have a small footprint, as they are occupying the same space as a person. Several components make up a robot, including motion controllers, sensors, servos, the processing logic, and so on. FPGAs are often the heart of the system and must combine adequate processing capabilities with the smallest possible sizes. In order to address this, an optimized architecture with a larger capacity but smaller physical package is required. Many low-density FPGAs have small packages but lack adequate logic resources, while current mid-range architectures lack smaller size packages and often do not have enough 3.3 V I/Os. Key features such as a large number of 3.3 V I/Os, large quantities of DSP blocks, embedded memory, and interfaces to newer memory standards are needed in smaller physical packages. Thus, a newer FPGA that is optimized for mid-range densities in smaller form factor packages enables small footprint solutions.
The requirement for portability is also becoming more prevalent. Some assembly line tasks require the use of handheld sensors or cameras to inspect hidden cabling or verify component connections. The increasing use of thermal image sensors to detect defects such as hot spots in electrical wiring is becoming commonplace. These thermal cameras are an example application where portability is required. An FPGA is often used to perform the image processing a thermal sensor detects. For an industrial requirement, the camera is likely more complex than a low-end thermal camera. This could be because of the higher resolution of the sensor, some processing-to-detect fault patterns, a high-resolution screen on the camera, or wireless connectivity. All these additional functions are often beyond the capabilities of low-end FPGAs. The FPGA must not generate significant heat or it will disrupt the thermal image sensor. In addition, for the camera to have adequate battery life and be compact in size, a lower power, small form factor, mid-range FPGA must be used. A mid-range FPGA with low power consumption and a small package size is critical to enable this type of design (Figure 1).

[Figure 1 | Small size, lower power, mid-range density FPGAs.]
Both examples discussed demonstrate the efficiency requirements needed for these new types of solutions: lower power, small physical packages, and optimized mid-range density architecture. Figure 1 shows an example of FPGA devices that meet these requirements.
Next, we must consider the smarter solution requirements and their application challenges. In many industrial automation systems, the controls for the motors are the brains of the system and current solutions often have a controller for each motor. These systems tend to have built-in human-machine interface (HMI) panels or switches to set up and control the motor. To enable the next level of efficiency, these controls must be connected to the cloud and other sensors to extract the maximum possible efficiency. However, making the leap from a closed system to an open networked system requires not only adding the network interfaces, but also the security infrastructure. Many hardware engineers believe security is a software problem, but nothing could be further from the truth. The data security of a system is of paramount importance, and hardware architects need to take responsibility for solving this issue.
So, what does it mean to secure a networked system? The FPGA is typically the heart of these systems and needs to adequately address the security of the system. Security needs for these applications usually fall under two categories: data security and design security. By data security, we mean the communication into and out of a system or design — if the design will be networked and connected to the cloud, it is essential that the data communication links be secure. By design security, we mean that if there is valuable IP in a FPGA, it must be protected so that others cannot extract the bit file and encryption key or reverse-engineer the function. Both of these security requirements should be addressed at the hardware level; if left to software, the system will be much more vulnerable to a cyberattack.
Because data security is paramount for networked equipment, we will focus on this requirement. To ensure data communications are secure, the information being sent must be encrypted and the data on the receiving side decrypted. But these requirements are only the high-level requirements. A specific algorithm and keys are required as a base in order to provide the encrypted data. There are many common algorithms, including AES-256, SHA, ECC, and others. To utilize these algorithms, they must be based on a key. For connection to the cloud, a dual-key strategy must be employed: this is referred to as public key infrastructure (PKI). It is based on using both public keys and private keys. Every node on the network has a public, certified key that is signed or approved by a trusted third party, and every node also has its own private key that only they know about. When sending secure communication, you use the node’s certified public key that you are sending data to as well as your private key to encrypt the data. Only the node with its public and private key will be able to decrypt the data. This is a basic description of how data to the cloud is secure, but a critical issue in this procedure is ensuring that the private key is not stolen. The protection of private keys needs to be addressed in hardware, not in software, and many systems are vulnerable because this is often overlooked.
There are numerous hardware components that can protect a key. The most secure system is one in which a physically unclonable function (PUF) is designed into the FPGA device. The PUF leverages the unique attributes of each individual silicon die, and is like a biometric identifier of the device. Using a PUF, non-volatile memory (NVM), and an on-chip random number generator (RNG), one can create the most secure private key. Without a PUF, a human must be relied on to program a key into a device or have keys generated outside the device, and these keys are likely to be stored somewhere; these are points of vulnerability that can lead to cyberattacks.
An early example of a new class of mid-range density FPGAs is the Microsemi PolarFire family, which is designed to protect private keys and perform completely secure data communications. The functional blocks of the device are shown in the following illustration (Figure 2).
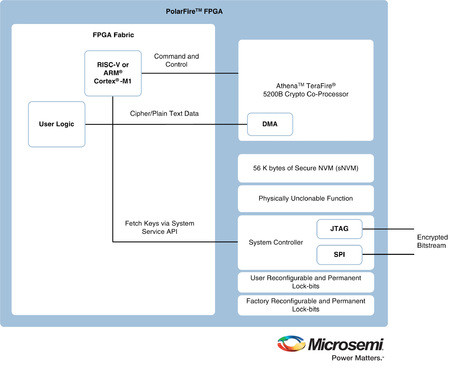 [Figure 2 | PolarFire FPGA with Data Security Processor, PUF, RNG, and Secure Non-volatile Memory]
[Figure 2 | PolarFire FPGA with Data Security Processor, PUF, RNG, and Secure Non-volatile Memory]
This type of device makes securing data communications much simpler. All the key building blocks are on the chip, including a cryptographic processor, PUF, key storage, and RNG. The designer simply needs to program the processor to generate the key based on the on-board PUF, then select the encryption algorithm to be used (such as AES-256), and the crypto processor does the rest. Very little of the FPGA fabric resources are used to enable the secure communications, leaving the majority of the FPGA device functionality to implement the specific design.
As the challenges of the workplace continue to evolve, so too must the suppliers who design and manufacture this equipment. Mid-range density FPGAs are now available to address the new challenges that industrial automation vendors are facing, including more processing power in smaller form factors, lower power, and data security. No longer are designers forced to sacrifice cost and power efficiency in order to achieve the necessary performance and multi-layered security that are required today and in the future.
Microsemi
LinkedIn: www.linkedin.com/company/microsemi
YouTube: www.youtube.com/user/MicrosemiCorp





