Secure Flash - The Cure for Insecurity in Connected Automotive and Industrial Applications - Part 2
April 06, 2020
Blog

In part 2 of this series, we will cover Secure Flash, the next generation of smart memory. Designing secure embedded systems, whether using eFlash or external Flash, is an onerous endeavor.
Designing secure embedded systems, whether using eFlash or external Flash, is an increasingly onerous endeavor. This section highlights some important considerations to help guide design and development efforts.
In general, there are three elements needed in systems designed for end-to-end security:
· Protection mechanisms for preserving the integrity of code and critical data by preventing it from being deleted, changed or corrupted through various means
· Detection mechanisms for revealing when code and/or critical data may have been altered by some unauthorized means
· Recovery mechanisms for restoring the integrity of any code and/or critical data that has been altered by some unauthorized means
Engineers should design systems that address all of the threats identified in the STRIDE model (see Table 1). This model, summarized in the following table, provides a practical way to understand potential threats and how to counter each with various security provisions.
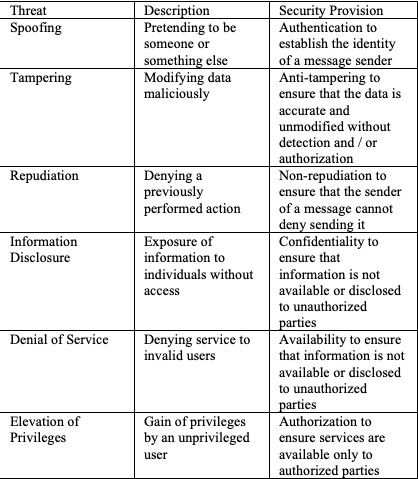
Table 1: The STRIDE model outlines the threats that secure systems need to address.
Secure product designs require establishing a Trusted Execution Environment (TEE) founded on a root-of-trust. The TEE provides the means to verify the authenticity and integrity of all components and subsystems before using them. Here are some best practices for creating such a secure design:
· Implement the root-of-trust in hardware to create a secure foundation
· Fortify this foundation with authentication and encryption
· Secure the value chain end-to-end for all connectivity, network and cloud components
· Provide immunity to side channel attacks and fault injection techniques
· Conduct an independent vulnerability and risk assessment of the system
· Continually monitor for anomalies in real-time
· Implement processes for countermeasures (e.g. secure update)
Figure 2 shows how implementing the root-of-trust in a system can involve making a tradeoff between risk and cost. As might be expected, software-based designs are the least expensive—and the least secure. What is not shown are the indirect costs of insecure embedded systems, and those very real costs make it easy to justify hardware-based designs that maximize security.

Here is how the National Institute of Standards and Technology’s Computer Security Resource Center explains the advantage of implementing roots of trust in hardware: “Roots of trust are highly reliable hardware, firmware, and software components that perform specific, critical security functions. Because roots of trust are inherently trusted, they must be secure by design. As such, many roots of trust are implemented in hardware so that malware cannot tamper with the functions they provide.”

Advances in technologies are continually driving down the cost of ICs leading to a reduction in the cost of systems incorporating next-generation ICs. Such is the case for external Flash with the advent of secure “smart Flash” that reduces the effort required to implement the root-of-trust in hardware and incorporate other desirable capabilities.
Secure Flash: Next-Generation Smart Memory
Semiconductor foundries are spending considerable effort pursuing small-geometry embedded Flash, but no viable solution has yet to emerge. Small-geometry RRAM and MRAM technologies have been explored extensively as eFlash alternatives, but these are not yet viable owing to data integrity and cost challenges, respectively, especially for mission-critical applications requiring high reliability at high temperatures. As of this writing, it is not clear when (or if) these or any other technologies will be able to deliver embedded memory in volume production.
The inevitable change caused by shrinking geometries has created the need for a new type of secure channel where bits can be exchanged between the HSM inside the MCU and a cryptographically secure region within an external storage device. One promising solution is to employ the converse of the current practice of integrating various types of memory into processors but instead integrating a processor into a memory ICs to create smart memory. Figure 3 shows how the secure Flash is able to establish an authenticated and encrypted Secure Processing Environment with the host MCU.
This trend in next-generation smart memory holds the potential to bring revolutionary changes to the electronics industry. For embedded systems, the advances will focus on NOR Flash, which is an ideal type of non-volatile memory for storing code based on its durability and fast random read performance.
Secure NOR Flash, or more simply secure Flash, provides hardware-protected secure storage for security keys, certificates, password hashes, application-specific data, configuration data, code version information and biometric sensor data for authentication. Secure Flash can also support authenticated and encrypted transactions to protect against unauthorized access and other security threats.
Current state-machine based memory architectures, by contrast, do not offer the same versatility and performance as one with an embedded processor. For example, robust security requires strong encryption and that, in turn, requires considerable processing power. An embedded processor can also support other security-related requirements, including HMAC key generation and storage, and monotonic counters, as well as provide protection against attacks on firmware, boot images and system parameters.
Embedding processing power in memory can optionally facilitate the integration of logic to add specific functionality and/or to offload the workload of a system’s host MCU. For example, the embedded processing can enable creating a hardware root-of-trust that prevents modification, manipulation and other security attacks on the stored code and data. Or the processor could run various algorithms on raw data, including those used for machine learning, before storing the results needed by the system’s other functions.
Additionally, for security regulations that can be satisfied partially or fully by code running in the smart memory’s embedded processor(s), compliance can be certified for new systems more easily. This holds the potential to dramatically accelerate the time-to-market for new products by simplifying the design and development effort required.
In part 3 of this series, we will cover design issues related to secure embedded systems using external Flash.
About the Author
Sandeep Krishnegowda is marketing and applications director of the Flash Business Unit at Cypress Semiconductor Corp. He has worked in Cypress’ memory products division for more than ten years in a variety of engineering, management and marketing roles. He earned an MS in Electronics and Communication from Rensselaer Polytechnic Institute and a BE in Electronics and Communication from Visvesvaraya Technological University.




