New functionality in RTOSs puts the focus on security
December 14, 2016
From its humble beginning as an interrupt-driven, multitasking kernel with some I/O support, the modern real-time operating system (RTOS) has evolved...
From its humble beginning as an interrupt-driven, multitasking kernel with some I/O support, the modern real-time operating system (RTOS) has evolved into an essential, sophisticated element for the development of connected embedded systems in the Internet of Things (IoT). Of course, many functions have been added over the years. For today’s embedded systems, the most compelling are new security features targeted to prevent breach by hackers, as well as theft and compromise of data and control. For developers, the RTOS now represents a platform on which they can build solid, reliable, safe, and secure systems.
As a platform, an RTOS provides many of the services required by embedded real-time and connected systems. These include interrupt-driven, real-time response, as well as other capabilities such as an integrated graphical user interface, wireless and network communications capabilities, file system management, internal inter-thread messaging, and more. These levels of complexity come built-in so the developer doesn’t have to understand or concentrate on implementing them. Instead, developers can concentrate on building their value-added applications on top of the services and capabilities provided. This is aided by the existence of a standard API, which makes it much easier to move to other processors. Once the RTOS runs on a given CPU, the application code can be ported over. Since it runs via the same API, there is no need to change it.
Processor support is also making the use of an RTOS more advantageous, and also has implications for security. Many of today’s RTOSs come matched to hardware platforms that offer a ready, fully functional development environment. Some vendors offer their RTOS bundled with a selected processor board in a development kit, while others have pre-qualified their RTOS to run on boards offered by the semiconductor manufacturer. In either case, the developer gets a ready-made environment to start adding innovation.
Association with hardware brings security advantages
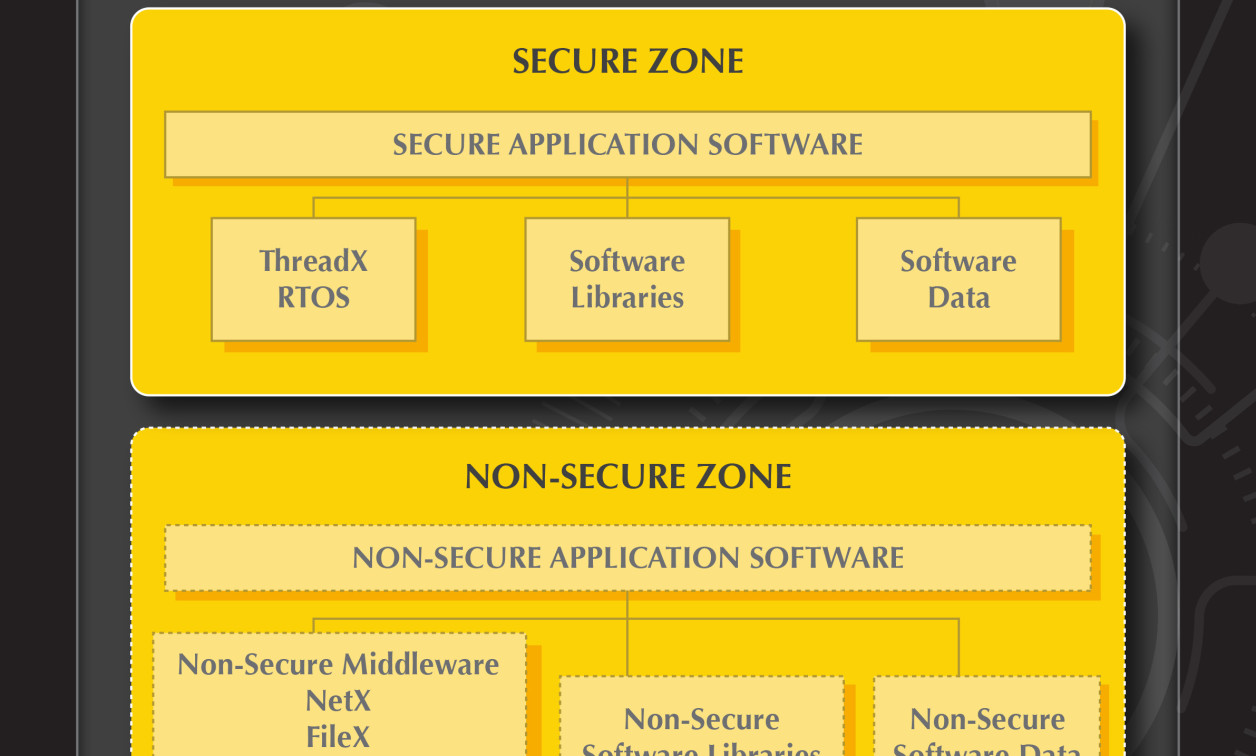
This close association between the RTOS and underlying hardware can have additional advantages because of the security features processor vendors are building into their hardware. This aids the secure memory management that RTOSs use to protect areas from invasion. For example, Express Logic’s X-Ware Secure Platform can protect trusted code from errors that might occur within other code while enabling the trusted code to interact with the entire system. With the ARM Cortex-M’s MPU, it can assign memory range (partition) boundaries to non-trusted code, preventing that code from accessing any code or data outside of its own partition. This prevents errors that might be present in that code from impacting the non-trusted code itself and from impacting trusted code or the RTOS.
The ARMv8-M architecture follows a similar protection process, except that the ARMv8-M is much more efficient. It provides a hardware implementation of all features necessary to achieve the same benefits. ARMv8-M enables the RTOS to assign partition boundaries to multiple code regions, enabling non-trusted code to be “confined” to those regions and thereby prevented from accessing trusted regions or the RTOS itself. Memory protection methods are also available for use with MPUs that do not have such hardware support. The key is to set up secure address areas to make sure that nothing can come in to alter or hide among approved code.
Secure communication protocols now integrated into advanced RTOSs
Advances in securing network communications include secure protocols such as the Transport Layer Security (TLS) protocol, which helps communicating systems mutually set up encryption for secure data transfer. This and other security communication protocols have become integrated with today’s advanced RTOSs to protect data from eavesdropping and tampering. TLS can be used with a number of different higher-level protocols such as HTTPS and SNMP, making it a very versatile tool for security. And, of course, encryption and security are also vital for implementing a secure boot loader for updating the core application code when needed.
Having proven security features as integral parts of an RTOS development platform goes a long way toward helping development teams build reliable and secure embedded applications — applications whose connectivity in the national infrastructure is becoming an ever more important factor in daily life.





